More Junkmail from Bob!
Dragonflies
The globe skimmer, or wandering glider, is probably the most widespread dragonfly on earth.
(J.M.Garg... took this picture.)
http://en.wikipedia.org/wiki/Globe_Skimmer
A guy named Charles was living in the Maldives, and figured out that these dragonflies manage to migrate from India to East Africa and back every year, following the rain. This migration is probably the longest of any insect -- about twice as long as the North American monarch butterfly migration.
http://en.wikipedia.org/wiki/Monarch_butterfly
Here is Charles -- he's a good speaker. TED has a lot of good speakers.
http://www.ted.com/talks/charles_anderson_discovers_dra...
The most amazing part of the Global Skimmer migration is the fact that they manage to get by the Somali pirates.
http://seattletimes.nwsource.com/html/nationworld/20112...
If you'd like to sail through the area, you might be able to join Lo Brust's convoy.
http://www.noonsite.com/Members/val/R2009-12-19-1
Real ID
According to the Real ID Act of 2005, the Department of Homeland Security is in charge of state driver license requirements. This will prevent U.S. drivers from blowing themselves up, so they can instead meet a peaceful death from drunk drivers.Unsurprisingly, Homeland Security made its requirements just a bit onerous. Most states have ignored the Real ID law so far, even though the federal government has extended the deadline for compliance a few times. After the latest extension, all states are required to comply with the Homeland Security driver license rules by 2011.
As of last fall, 25 states had passed laws or resolutions to ignore the Read ID Act, including Utah.
http://www.sltrib.com/news/ci_14429755
It is a state's right to do that. The federal law only says that a non-Homeland Security approved driver licenses cannot be used for any federal activity, such as getting on an airliner (Photo by Alice)...

...or driving a nuclear submarine.

The Real ID law has been welcomed by those it serves in compliant states, such as Florida...
http://www.tampabay.com/news/publicsafety/article1075902.ece
and Nevada
http://www.lvrj.com/news/real-id_-one-small-step-at-a-t...
The cost for complying with Real ID is only about $4,000,000,000, which naturally will be paid by the state governments.
http://en.wikipedia.org/wiki/REAL_ID_Act
http://www.npr.org/templates/story/story.php?storyId=12...
Restaurant Music
A guy named Mark has a restaurant in Tucson called Chuy's Mesquite Broiler. A while back, Mark had a karaoke night and hired a group to come into the restaurant and put it on. The music publishing industry (maybe ASCAP, BMI and/or SESAC) decided Mark hadn't paid them, so they sued and won $48,694 from Mark, just because 14 of their songs were played in his restaurant, once. That sure makes me want to go buy some CDs.http://www.zeropaid.com/news/87433/unlawful-use-of-copy...
Cell Phone Brain Cancer
I may have mentioned this before, but cell phones don't put out enough radiation to cause brain cancer. There is just not enough energy to alter chemical bonds in cells.http://arstechnica.com/science/news/2009/12/who-needs-s...
Furthermore, there has been no increase in brain cancer since before the age of cell phones. If cell phones were even a minor cause of brain cancer, we'd see it in the statistics.
However, cell phones can and do cause death. It happens when you talk or text or browse when you should be driving.
In other health news, few people were surprised to learn that those who watch a lot of TV are less healthy that those who don't.
http://www.telegraph.co.uk/health/healthnews/4360691/Re...
This does not mean that TVs cause brain cancer. It means that TV ads suck the intelligence right out of your brain, causing health problems.
However, Diet Cokes might be safe to drink while you're watching TV. Cancer is strongly related to diet, but not aspartame.
http://www.cancer.gov/cancertopics/factsheet/risk/aspartame
And, the likelihood of being blown up by a lithium battery is negligible.
http://hardware.slashdot.org/story/10/02/11/2252214/FAA...
Transistors
Once upon a time, people used vacuum tubes in place of integrated circuits. Vacuum tubes came in many forms, used as diodes, amplifiers, and switches.A diode allows electricity to flow one direction but not the other. Solid state diodes (crystal diodes) were made even before vacuum tubes were popular, in the late 1800's. My high school chemistry teacher, Mr. Jolly, made a radio receiver with a homemade crystal diode, a coil of wire, and a homemade capacitor when he was a World War II prisoner of the Japanese.
When I was about 9 or 11 years old, I made a crystal radio with some old radio parts and a diode that I bought. It didn't even need a battery. The first time it worked, I heard a crazy guy, yelling and carrying on, saying that the only good use for the Apollo space program was to send all the blacks (he used a more colloquial term) to the moon and leave them there.
Even at that age, I thought the guy was nuts, and I must be receiving from Mars, or at least another country. It turns out that it was Dinty Moore, a local preacher, on an AM station that nobody listened to, its transmitter about a half mile from my house.
It's nice to see traditions upheld. Today's AM radio talk shows are also frequently populated by nuts. To illustrate my point, even I have spent thirty minutes on a radio talk show a couple of times. But I didn't mention politics.
Triodes and other vacuum tube variations are not as simple as diodes. They work, more or less, like an amplifier or a relay. They take a small input and produce a large output. More specifically, a small change in the input voltage will make a large change in the output voltage. This makes them useful for switching, as in digital computers and electric controllers, and amplifiers, as in radio transmitters and stereos. There are many variations on these themes.
In 1947, some people (John and Walter, with some help from William) at Bell Labs made a transistor. This was pretty impressive, because it was the first transistor ever made. It did the job of a vacuum tube, but it was smaller, took a lot less electricity to operate, and would eventually be a lot less expensive to make. Finally, they could make a desk-sized computer:


Since then, transistors have been made smaller and faster, packed together into integrated circuits, to the point that my new CPU has 731 million transistors in a single chip.
 hires
hiresIt has 1136 wires coming from the chip to the rest of the computer.

My last CPU only had 775 pins, so I ended up getting a new motherboard. As usual, several of my applications started complaining. Among them was Microsoft Office 2003. (I had upgraded to that because I was having trouble getting Office 97 installed on my Windows-7 laptop, and I prefer to keep the same version on both computers.)
Office 2003 said my computer had changed, and I needed to re-activate Office. So I did, or at least I made a valiant attempt. Microsoft's computer said I had activated Office too many times, and I should call them. This is normal procedure for me, because I change computer hardware pretty often. So I called up. They said they couldn't activate it.
My copy of Office 2003 was bought and paid for, and was licensed for up to 10 computers. Since I was not using it on nearly that many computers, I was completely legal. I explained this to Microsoft people from Bellevue to India. They agreed that I had a legitimate copy. They even looked up when I bought it from them. But they said something was wrong with their system and it wouldn't give me a code.
Meanwhile, Word and Outlook partially shut down so I couldn't save files or send mail. That's a nice way to treat customers.
After three phone calls and over an hour on the phone over a couple of days, I gave up and figured out how to install SP2 of Office 97 on Windows 7. They can keep their lousy Office 2003, 2007, 2010, and anything else that doesn't like my new CPU. My next migration will be to Open Office, if it will do what I need. It's free, and they don't shut off my software.
http://why.openoffice.org/
I have been considering upgrading from Windows XP to Windows 7. But now I am afraid that Windows 7 will get tired of me upgrading my hardware and shut down. This fear was reinforced a couple of weeks ago. I was on a boat with my Windows 7 laptop, and a window came up saying that Windows had been modified, and it its functionality would be limited until I re-activated. This made me nervous, because I don't normally carry a Windows 7 disk or product key around with me. Microsoft was just planning to shut my computer down for a few days for no reason.
But I closed the window, and everything was normal. I wonder what will happen when Chinese hackers figure out how to shut down Windows 7 computers using the Genuine Advantage "feature" of Windows. It seems like it should be fairly easy to write a trojan to do this.
Better yet, if China (or Russia or anybody) could redirect Windows Genuine Advantage traffic to their own servers, they could shut down every Windows 7 system on the internet. That would be a real cyber-attack.
Back to transistors. Last year, a group of researchers from Korea, U.S., and Germany built the world’s first functional molecular transistor - a transistor made of a single molecule.
http://arstechnica.com/science/news/2009/12/researchers...
It's a little confusing, after this article in 2004, "Scientists Help Develop First Single Molecule Transistor."
http://www.sciencedaily.com/releases/2005/06/0506080555...
The difference is the word "functional." The new molecular transistors were actually built, "wired," and tested thoroughly. It's a big step from the ones in Liverpool, which were a huge step in themselves. Molecular computers are still some distance in the future, but they do look possible, and might even be practical.
http://opa.yale.edu/news/article.aspx?id=7169
German Internet Data
In 2008, Germany passed a law, following a European Union directive, requiring data email and phone call data to be saved for at least six months in case it is needed for law enforcement. A lot of people in Germany didn't like this. Apparently the German high court doesn't either. They overturned the law, declaring it unconstitutional. They went further and ordered that all the data saved so far be erased.http://www.spiegel.de/international/germany/0,1518,6812...
The U.S. government doesn't have to worry about this. They are above the law when it comes to "national security" concerns such as intercepting email and phone calls. There are laws against this, but nobody in charge seems to care. It surprises me that this is one area where the Democrats and Republicans agree.
http://www.wired.com/threatlevel/2010/01/fbi-att-verizo...
In an example of transparent government, the federal government has been trying to keep secret the identities of lobbyists whose efforts got phone companies retroactive immunity from warrantless wiretapping. A federal appeals court has rejected a government claim of "lobbyist privacy," so maybe the government transparency will be a little easier to see through.
http://www.eff.org/press/archives/2010/02/09
When a school gets into the act of illegal surveillance, a LOT of people get wound up. That's probably a good thing.
In Pennsylvania, a high school provided all the students with laptops. The laptops were set up so that the people at the high school could turn on the laptop camera and monitor what was happening on the laptop. The students faced expulsion if they disabled this. As you might expect, since it was so easy to do, some people at the high school decided to take pictures of the kids at home. This is considered very bad manners.
This was not an evil plot by anyone at the high school. It was more a problem of technical ignorance by the people who put together the specs and policies of the student laptops. I'm guessing other high schools will catch on pretty quick.
http://strydehax.blogspot.com/2010/02/spy-at-harrington...
Swift Bank Data
When you wire money anywhere in the world, it uses the Swift data system. The U.S. has been accessing European Swift data, for national security concerns, and was trying to get a 9-month extension. Europe said no, despite lots of phone calls by Timothy Geithner, Hillary Clinton, and Joe Biden. The European Members of Parliament said there were not enough privacy safeguards.I'm outraged! How could they possibly worry about the U.S. government violating privacy?
http://news.bbc.co.uk/2/hi/europe/8510471.stm
Mars Photos
In August 2005, the first Atlas V rocket ever used by NASA launched the 2-ton Mars Reconnaissance Orbiter (MRO) from Florida toward Mars.
The Atlas V rocket has to be pretty big to do that, but it has only about the quarter of the power of the Saturn V rocket they used to get people to the moon. (It's not easy to compare these two, since they have different characteristics, but the Saturn V can deliver about 4 times the payload into low earth orbit.)
The following year, MRO made it into Mars Orbit and started sending back data and photos. It's now flying around Mars at a altitude of 150 to 200 miles.
http://en.wikipedia.org/wiki/Mars_Reconnaissance_Orbiter
Mars is pretty interesting to look at. There are things happening on the planet. There is wind, ice (mainly carbon dioxide ice), dust storms, and the new Walmart at the east end of Valles Marineris.
http://en.wikipedia.org/wiki/Valles_Marineris
The "High Resolution Imaging Science Experiment" (HiRise) team has a whole bunch of hi-res photos from Mars, hosted at the University of Arizona.

These are really good!
http://hirise.lpl.arizona.edu/katalogos.php
They also have declared them to be public domain, which is a very good idea. It is dumb when an organization that can only benefit from the publicity of its photos restricts their distribution. That happens surprisingly often.
Russian Nuclear Lighthouses
The north coast of Russia includes a few thousand miles north of the Arctic Circle. Ships can use follow this coastline for a shorter way to go between the eastern and western Russia. Now, navigation is easy with GPS and the Russian counterpart Glonass.http://en.wikipedia.org/wiki/GLONASS
But before GPS, navigation was not so simple. In the 1960's and 1970's, the Soviet Union needed some navigational aids for ships sailing across the northern coast. They built some lighthouses, but these were in uninhabited areas, in many cases very far from civilization.
So they built autonomous lighthouses. To power the lighthouses, the Soviets built small, lightweight nuclear reactors. The reactors would run unattended for years. The lighthouses automatically turned on their lights when it was dark, and sent radio signals to nearby vessels. I'm not sure whether the lighthouses were originally staffed by people.
The polar nuclear lighthouses were abandoned after the collapse of the Soviet Union. The lighthouses have declined in the past 30 years, succumbing to nature and looters. The looters tend to ignore the "Radioactivity" signs and salvage whatever they can.
Here are some photos from one of the lighthouses, and some information on the lighthouses.
http://englishrussia.com/?p=2198
Sometimes the site is too slow to show the photos. Here's another copy if you can't get the originals:
lighthouse
Cyber Insecurity
The Bush administration launched the Comprehensive National Cybersecurity Initiative a couple of years ago. It is "a sweeping program to protect the government and critical civilian networks from cyberattacks." The government classified everything, and wouldn't even tell Congress what the money was being spent on.Obama has not declassified the project, as one would expect from transparent government, but they did release a 5-page summary of the program. I think they should release the rest of it right away, because they need some help. There are some pretty dumb ideas in the summary. It appears that those politically appointed experts that operate behind closed doors need to get out into the internet and see what's happening in the real virtual world.
http://arstechnica.com/tech-policy/news/2010/03/obama-a...
http://arstechnica.com/security/news/2010/02/obama-admi...
In other transparent government, the Health Care negotiations continue behind closed doors.
http://biggovernment.com/publius/2010/01/05/c-span-asks...
Connected Nation
"Connected Nation, Created by Telco Lobbyists, Gets Millions in Government Funding to Hide Broadband Data from the Government"http://www.techdirt.com/articles/20091223/1246267491.shtml
Child Pornographers
1. It is easy to take a picture with a cell phone and send it to someone.2. Most teenagers have cell phones.
3. It is very common for teenagers to send pictures of themselves to friends.
4. It is not uncommon for teenagers to send risqué pictures of themselves to friends.
These are all facts. Unfortunately, some people think that a teenager who sends an R-rated self-portrait to a friend should be prosecuted for child pornography, sent to jail, and labeled a sex offender for life. Some people who think this way are prosecuting attorneys. Maybe we should also make the girls involved wear a scarlet P (for Pornographer) for the rest of their lives. Or we could go with a more traditional punishment -- lashes.
http://www.businessweek.com/news/2010-03-03/saudi-woman...
Some kids are going to do this only because it can be easily done. Push a couple of buttons on your cell phone, and you've sent a pic of yourself to a friend. This does not make them criminals, perverts, or even Democrats. They shouldn't do that, and they should be punished, but by their parents, NOT by the police. The police have plenty of real police work to do.
http://www.techdirt.com/articles/20100115/1500557776.shtml
http://www.reuters.com/article/idUSTRE60E51A20100115
http://www.nbcchicago.com/news/local-beat/indiana-middl...
http://abcnews.go.com/TheLaw/story?id=5995084
http://articles.sfgate.com/2009-01-29/living/17331420_1...
UAV Degree
The University of North Dakota has a pretty strong aviation program. They have just come out with a bachelor's degree in Unmanned Aircraft Systems and Operations. I think that would be interesting.http://www.avweb.com/eletter/archives/avflash/1545-full...
RSA Encryption
In 1978, three people named Rivest, Shamir, and Adleman published a public key encryption method in the Communications of the ACM. I think they had published some papers on the project the previous year, too. Here's a copy of the article:RsaPaper.pdf
With private key encryption, both the encryptor and decryptor have to have the same secret key. This requires an initial secure communication to send the key. In public key encryption, you can let everybody have a public key and use it to encrypt messages, but a secret corresponding private key is required to decrypt a message.
20 years later, in 1997, the RSA encryption algorithm, named after the three authors of the 1978 paper, was in common use as a standard, secure public key encryption method. The U.S. government prohibited the export of any software using RSA encryption keys longer than 56-bits, even though encryption software using longer keys had been developed outside the U.S. and was readily available worldwide. The RSA 56-bit encryption challenge had been broken a few times.
http://www.rsa.com/press_release.aspx?id=716
The largest 56-bit integer you can have is 72,057,594,037,927,936. Cracking the encryption requires finding the prime factors of a large number such as this. It takes a while.
Technology has progressed. Last month a group from Switzerland, Japan, Germany, France, the U.S., and the Netherlands factored a 768-bit RSA key (modulus). The 232-digit number they used was slightly larger than the 56-bit key of 1997:
123018668453011775513049495838496272077285356959533479219732245215172640050726
365751874520219978646938995647494277406384592519255732630345373154826850791702
6122142913461670429214311602221240479274737794080665351419597459856902143413
The previous record was a 200-digit 663-bit number in 2005.
From the paper: "The following effort was involved. We spent half a year on 80 processors on polynomial selection. This was about 3% of the main task, the sieving, which was done on many hundreds of machines and took almost two years. On a single core 2.2 GHz AMD Opteron processor with 2 GB RAM, sieving would have taken about fifteen hundred years. This included a generous amount of oversieving, to make the most cumbersome step, the matrix step, more manageable. Preparing the sieving data for the matrix step took a couple of weeks on a few processors, the final step after the matrix step took less than half a day of computing, but took about four days of intensive labor because a few bugs had to be fixed."
The authors predict that 1024-bit numbers will be factored over the next decade in academia, and it is probably a good idea to move to 2048 encryption over the next three or four years. I assume that governments are better at this that universities.
rsa768.pdf
More information on RSA:
http://en.wikipedia.org/wiki/RSA
To encrypt your own files on a hard drive, you don't normally need public key encryption. AES is a common, secure method for private key encryption.
http://en.wikipedia.org/wiki/Advanced_Encryption_Standard
AxCrypt is a pretty good (and free) program for AES encryption.
http://www.axantum.com/AxCrypt/Downloads.html
Norfolk Ditching
In November, a Westwind 1124a jet took off from Samoa on a medical flight to Melbourne, Australia. They planned to stop at Norfolk Island for fuel. They ended up landing in the ocean, intentionally, because of the weather. Here is the report.http://www.atsb.gov.au/media/1345477/ao-2009-072-prelim.pdf
Terrorists are Everywhere
A few weeks ago, quick thinking by the crew prevented a 17-year-old boy from using Jewish scriptures in a leather container to blow up a U.S. Airways Express airliner. The flight from New York to Louisville landed at Philadelphia so the young terrorist from White Plains, along with his 16-year-old sister, could be interrogated by Homeland Security. They were allowed to go on to Louisville later in the day.http://www.philly.com/philly/news/20100121_Plane_lands_...
A couple of weeks later in Philadelphia, the TSA narrowly avoided another disaster when a guy named Nicholas attempted to board and blow up an airliner using English-Arabic flashcards.
http://www.boingboing.net/2010/02/10/tsa-detains-middle...
The Philadelphia TSA also enjoyed some healthy criticism for forcing the developmentally delayed four-year-old child of a police officer to have his leg braces removed and attempt to walk through security without help from his parents.
http://www.philly.com/philly/news/local/84368492.html
To his credit, the boy's father does not intend to sue. He just wants the TSA to clean up their act.
Operation Exodus
Islamic terrorists have been operating in Bossier Parish, Louisiana, according to the Sheriff's office there. They have unveiled Operation Exodus to fight the terrorists and also prepare for natural and unnatural disasters.They plan to arm volunteers with shotguns, riot shields, batons, and a .50-caliber machine gun mounted on a "war wagon."

The training has begun.

They had 250-300 people at the initial meeting. The video:
http://www.bossiersheriff.com/public-view-news.cfm?id=781#
More info:
http://tpmmuckraker.talkingpointsmemo.com/2010/03/sheri...
http://www.bossiersheriff.com/public-view-news.cfm?id=781#
These people seem to have good intentions, but if they ever decide to overthrow the government they'll have to register with the state of South Carolina.
http://www.scstatehouse.gov/code/t23c029.htm
Buying Congress
A U.S. Congressman from Indiana named Steve founded a foundation in 2003 to award scholarships to college students. That was a noble undertaking. The Frontier Foundation has raised about $800,000.One small donation of $200,000 came from the Pharmaceutical Research and Manufacturers Association, the drug industry's primary lobbyist. The lobbying organization also hired Steve's son Ryan.
Congressman Steve goes even one step farther. His foundation (as of January) has never awarded a single scholarship. I understand that the foundation has paid for quite a lot of Steve's golf, though.
Unfortunately, after some hoopla regarding the Frontier Foundation, Congressman Steve won't be running for re-election. This is because of his wife's health and other personal reasons.
http://www.opensecrets.org/news/2010/01/rep-steve-buyer...
eBay Sculpture
Modern artist Caleb Larsen built a shiny black box with a computer inside. He named it "A Tool to Deceive and Slaughter," called it a sculpture, and put it up for sale.
The purchaser agrees to keep the box, or sculpture, rather, connected to the internet at all times. The box checks into eBay every 10 minutes to see if it is for sale. If not, the box starts an auction for itself.
There is no reserve but, but the starting bid is always what the box last sold for. A kickback of 15% of the gross profit goes to Caleb Larsen. The current owner pays the auction fees.
What happens if the owner doesn't do what he's supposed to? "Any failure to follow these terms without prior consent of Artist will forfeit the status of the Artwork as a legitimate work of art. The item will no longer be considered a genuine work by the Artist and any value associated with it will be reduced to its value as a material object and not a work of art." That's serious stuff!
Here's where you can find the current auction. It last sold for $6,858.
http://atooltodeceiveandslaughter.com/
Some Notable Links
Liar:http://www.zenmoments.org/my-favorite-liar/
Polyamory is wrong:
http://farm5.static.flickr.com/4059/4294...5.jpg...
20 Questions -- the computer is good!
http://us.akinator.com/
Anarchy
In Los Angeles there was a bookfair last January. It was the second annual Anarchist Book Fair, held at the Barnsdall Art Park, a facility of the Los Angeles Department of Cultural Affairs. To me, this seemed a little structured for a true anarchist.http://www.anarchistbookfair.com/node/18
If I were an anarchist, I think I would live in a missile silo.
http://www.wired.com/rawfile/2010/02/gallery-silo-3/all/1
A 64-year-old guy named Leroy Bunting got out of prison last August. He had been there about 27 years, spending 6 years in solitary confinement. Some human rights groups tried to make a victim/hero out of him, but I think if I were in prison I would prefer a private room, too. Bunting was jailed after a bank robbery and shootout in 1975, was paroled, shot someone (a parole violation), and was tossed back in jail about 1982.
Bunting changed his name to Ojore Nuru Lutalo, a more proper name for a cult figure, and declared himself an anarchist. He even had a speaking engagement at the Anarchist Book Fair. On the way back from LA to New Jersey, he took the train. Some people heard Lutalo talking on his cell phone and decided he was a terrorist.
More specifically, two passengers reported overhearing Lutalo's half of a cellphone conversation to the conductor, in which Lutalo said "haven't killed anyone yet" and "17th century tactics won't work, we have 21st century tactics." The conductor also stated that Lutalo was wearing a tan blanket, preventing her from seeing his body movements, and said he was connected with Al Quaida. Amtrak promptly called the Pueblo police and reported that Lutalo was making terrorist threats.
The police in Pueblo, Colorado arrested him and found "subversive material" in his baggage (from the subversive book fair). The FBI said it was from the Afrikan Liberation Army. The New Afrikan Liberation Front was incensed, claiming it was their literature and the FBI intentionally got their name wrong.
When I read this, I thought he would be an unlikely terrorist. I agree he may not be a nice guy, but he has served his prison sentence and is entitled to rob another bank before he goes back to prison. The Otero County DA apparently agrees, because he declined to press charges.
http://www.chieftain.com/articles/2010/02/04/news/local...
On the positive side, Mr. Lutalo's newfound fame might allow him to charge enough for his anarchist speaking engagements that he won't have to rob banks any more. He could become a law-abiding anarchist.
Internet Disconnect
Elsewhere in Pueblo, Colorado, a lady named Cathi was kicked off the internet after the Hollywood film industry, MPAA, or some incarnation thereof told Qwest she was downloading movies.But Cathi explained to Qwest that she was not downloading movies. Hollywood called her a liar, claiming she downloaded 18 movies and a bunch of TV shows including South Park. Qwest said if Cathi was accused of illegal downloading one more time, they would disconnect her and she would have a hard time getting internet from anybody else.
Cathi is a technical recruiter, and works out of her home. She needs the internet in order to make a living. She got in touch with cNet, who wrote some articles about her, garnering a lot of publicity. Qwest then decided "her network had been compromised" and she wasn't downloading movies after all.
All it takes to be booted off the internet is an unsubstantiated accusation by the movie industry? I think there is something wrong with that.
http://news.cnet.com/8301-31001_3-10444879-261.html
http://www.techdirt.com/articles/20100201/1014577990.shtml
Why would anybody pirate a movie, anyway?
http://farm5.static.flickr.com/4032/4369403959_fe90464b...
Nuclear Power
The U.S. Government may triple the amount of federal loan guarantees for nuclear power projects, from 18 to 54 billion dollars. This is far from certain, however. It is in the federal budget proposal, which has to undergo a lot of manipulation by politicians before it will become law.http://news.slashdot.org/story/10/01/31/1327238/Obama-B...
But they are getting started now, with an $8 billion loan guarantee for the Southern Company to build a new nuclear power plant near Waynesborough, Georgia. That money was in last year's budget.
http://online.wsj.com/article/SB10001424052748704804204...
Important Statistic
3 out of 4 people make up 75% of the word's population.Cell Phone Tracking
Your cell phone can be tracked, actively and retroactively. The Obama administration has argued that warrantless tracking is permitted because Americans enjoy no "reasonable expectation of privacy" in their (or at least their cell phones') whereabouts.Here's a good article about what's been happening.
http://news.cnet.com/8301-13578_3-10451518-38.html
Norfolk Backups
The city of Norfolk, Virginia got a lesson in disk backups last month when 800 of their 4500 PCs had most of the files on their hard drives erased. Someone slipped some malware into their network, probably not via the internet.http://www.pcworld.com/article/189679/city_of_norfolk_h...
Hexacopter
This is a cool electric model helicopter, complete with six independent, reversible rotors. It's amazing how far small computers, batteries, and electric motors have come in recent years. The software alone is impressive.http://www.youtube.com/watch?v=fyYujjP5J-k
Cryptome Takedown
Cryptome.org has published several guides for law enforcement from various large ISPs, explaining how law enforcement officials can access email or other internet records from the ISP customers. They recently published this one from Microsoft:http://www.wired.com/images_blogs/threatlevel/2010/02/m...
Microsoft did not like this. They ordered Network Solutions to shut down cryptome.org, claiming copyright violation (DMCA). Network complied, and killed the entire web site. This caused a minor uproar in the internet privacy community, and dozens if not hundreds of copies of the offending document were posted all over the internet. Within a day or two Microsoft said, "never mind" and Network Solutions put the cryptome.org back online.
http://www.wired.com/threatlevel/2010/02/microsoft-cryptome/
This is one of those things few people would have noticed had Microsoft not brought attention to it by trying to bury it. It's the Streisand effect.
Patriot Act
We now get to enjoy at least one more year of the Patriot Act.http://www.boston.com/news/nation/washington/articles/2...
Excellence in Broadcasting
Fox News does not know where the Australia cities Sidney or Darwin are. They are marginal with New Zealand.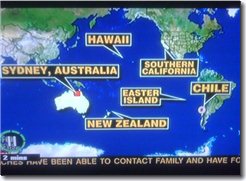
Chile Earthquake
Here is some real information, without sensationalization.http://www.nytimes.com/2010/02/28/world/americas/28quak...
BB Guns
The Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) seized 30 Airsoft BB guns from a store in Cornelius, Oregon. The BB guns did not have orange tips, which is easy to remedy.The other reason for the seizure, according to Special Agent Kelvin, was "With minimal work it could be converted to a machine gun." I think it would be just about as easy to convert a sewing machine into a hard drive.
http://www.koinlocal6.com/content/news/topstories/story...
I'm glad the government is protecting me.
Sorting and Searching
In Europe they decided that it is illegal for Microsoft to force Internet Explorer on Windows users. Instead, they have a browser ballot in which users get to select Google Chrome, Firefox, Safari, Internet Explorer, or Opera during Windows installation.http://www.browserchoice.eu/BrowserChoice/browserchoice...
These choices come up in random order. Or, at least, they are supposed to. In reality, they don't. For example, when the ballot is viewed using Internet Explorer, the Internet Explorer comes up in the rightmost position about 50 percent of the time. When the browser ballot is viewed with other browsers, the results are different.
With such a simple programming problem (arrange 5 things in random order), people naturally cried foul and accused Microsoft of cheating. But it turned out to be an innocent, if dumb, mistake.
Whoever programmed this decided to use a sort to arrange the browsers, but whenever there was a comparison, instead of comparing the strings, the sort would select one of the two strings with a 50-50 chance of one being greater than the other. For example, when it was time, in the sort, to compare "Firefox" and "Safari," it would return "Firefox" greater than "Safari" 50% of the time.
At first glance, it seems like a reasonable, if obtuse, way to generate a random order. However, some sorting techniques do not have an even distribution of comparisons. This technique will actually be much less than random using some sorting algorithms, and, since different browsers user different sorts, the results are different among browsers.
A proper way to do this is to assign each of the 5 browsers a random number, and sort them based on that number.
http://arstechnica.com/microsoft/news/2010/03/coding-er...
Amateur Physics Videos
Learn something new! Or at least see something interesting.http://amasci.com/amateur/physvids.html
Pico and Sepulveda
Pico and Sepulveda, where nobody's dreams come true. The music video:http://www.youtube.com/watch?v=znHA1rYxmN4
Perpetual Motion
In Odessa, Missouri, population 4,818, they have announced a plant to build home generators that run off magnets and require no fuel or outside power to generate electricity. Manna of Utah (an appropriate name) is the company that is coming into town with 3,000 manufacturing jobs and 1,200 more jobs in a research and development center. The mayor of Odessa, Tony Bamvakais, said the city has agreed to provide $90 million in revenue bonds to the company and has offered a plant site.The product is a home generator developed by Maglev Energy of Largo, Florida, which is leasing the technology to Manna of Utah. The Odessa mayor says it's not a perpetual motion machine, but it's so efficient that it keeps on producing power when it's unhooked from an outside power source.
http://www.kansascity.com/2010/02/18/1758530/odessa-mo-...
After a little cogitation, some people began to wonder if it's a good idea to violate the laws of physics.
http://www.kansascity.com/2010/03/02/1785362/generator-...
Pictures of Today!

Russellville, Arkansas nuclear power plant

Good shape, needs a little roof work

Danville, Kansas

This Old House.

Pictures from Merritt Island, Florida, three weeks ago

Pictures from North Star Mountain, Colorado, yesterday